Keycloak is an Identity and Access Management System that enables users to easily add authentication to secure services and applications without storing or authenticating users. Keycloak offers user federation, strong authentication, management, fine-grained authorization, and more.
Users use Keycloak for authentication instead of individual applications. Thus, you can stop worrying about login forms, user authentication, and user storage in your applications. Additionally, users logged into Keycloak do not need to do so again to access other applications.
Keycloak offers single-sign-out. Users just need to log out once to exit all Keycloak-using applications. Additionally, Keycloak can authenticate users using SAML 2.0 or OpenID Connect identity providers already in place.
Keycloak comes with built-in support for connecting to Active Directory or LDAP servers. Additionally, you can construct your provider if you have users in other stores, like a relational database. Administrators can centrally control every aspect of the Keycloak server through the admin console. Here, we have tried our best to cover all the sites similar to Keycloak.
Features
- Identity Brokering and Social Login
- User Federation
- Admin Console
- Account Management Console
- Standard Protocol and Authorization Services
There are up to 9 Keycloak Alternatives. The best alternative to 9-keycloak-alternatives is Duo, which is Free. The other best apps like 9-keycloak-alternatives are Google Authenticator, Yubico and Azure Multi-Factor Authentication.
Pricing
Keycloak Information
9 Best Keycloak Alternatives
Filter Alternatives
1Okta
Okta deals with the leading independent provider of identity that can help its users with significant tasks regarding their enterprises. This platform can let its clients get an adaptive security system that can protect them with the protection of their entire data. It can even permit its customers to access the Identity Cloud, allowing them to organize & secure their workflow experiences in real-time. Okta also facilitates its users to quickly adopt multiple advanced technologies to complete their required missions…
2Yubico
Yubico Authenticator enables users to securely store TOTP and HOTP credentials on a YubiKey, offering portable, multi-platform authentication. Developed by Yubico Inc., this program supports OATH credentials for major platforms like Google Apps, Amazon, Hotmail, Dropbox, Microsoft, and more. Even if your phone is compromised, your credentials remain safe when stored on a YubiKey.
Advertisement
IBM Access Manager is an all-in-one identity and access management platform that includes a suite of technologies for securely extending data centers to the Internet. Customers may use this solution to govern access and usage rights across a variety of resources, such as file servers, websites, databases, e-mail, Web Services, application hosting, apps, Web content, mobile devices, virtual machines, and more. Its robust network security safeguards networks, individual PCs, services, and businesses. With multi-cloud compatibility, it comes with the necessary…
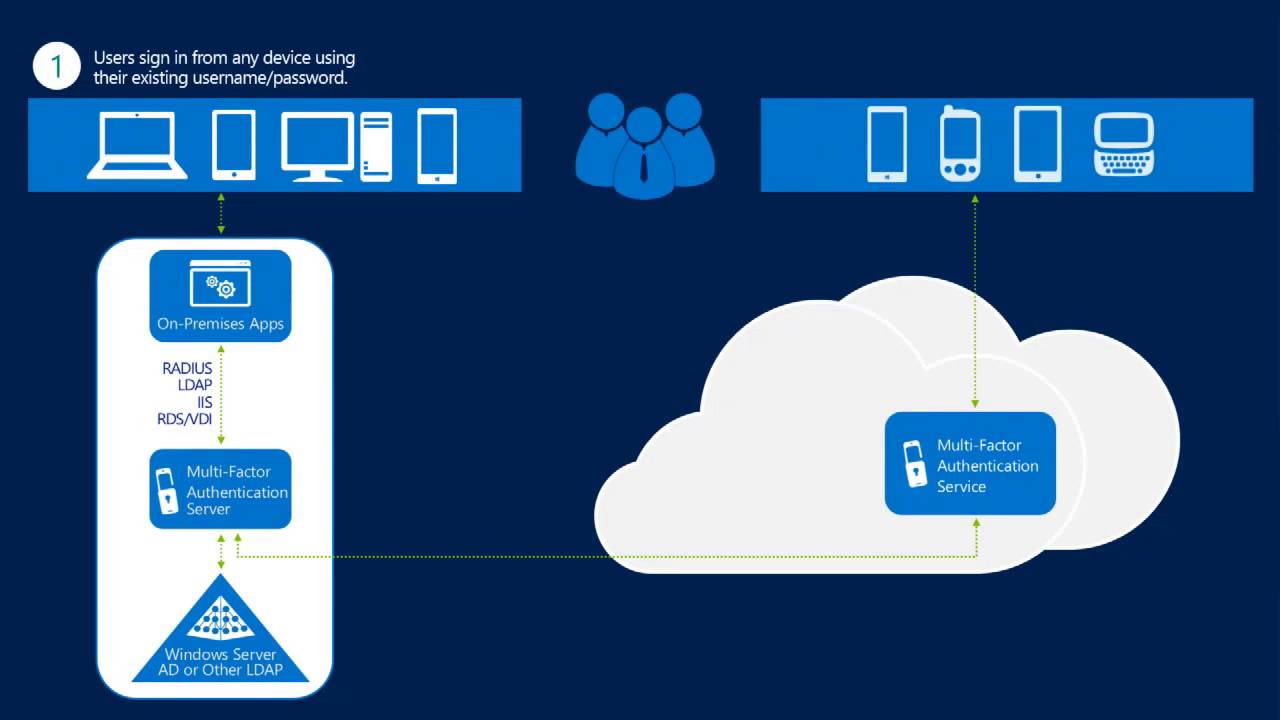
Azure Multi-Factor Authentication is a professional security and privacy program that gives you an extra layer of protection against identity theft. The program appears to be highly functional because, after logging in with your password, you must either enter a code sent to your phone or scan your fingerprint. There will be an unsecured vector to attack if you just utilize a password for user authentication. With the entire identity criteria, the program adds to the security, and your security…
Advertisement
Google Authenticator enhances security by generating two-step verification codes for your Google Account. Launched by Google LLC, this app requires users to provide a second form of authentication when signing in. It works offline, generating codes even without an internet connection, making it convenient for use on the go.
6Authy
Authy provides a two-factor authentication (2FA) service that sends text messages with verification codes for logging into protected accounts. The app allows synchronization across multiple devices, ensuring that you can access your codes from both your phone and computer. You'll receive notifications whenever someone attempts to access your account. When you log in to an account protected by Authy, you will receive a text message, which is one of the finest ways to implement two-factor security. It features a capability…
Advertisement
7Auth0
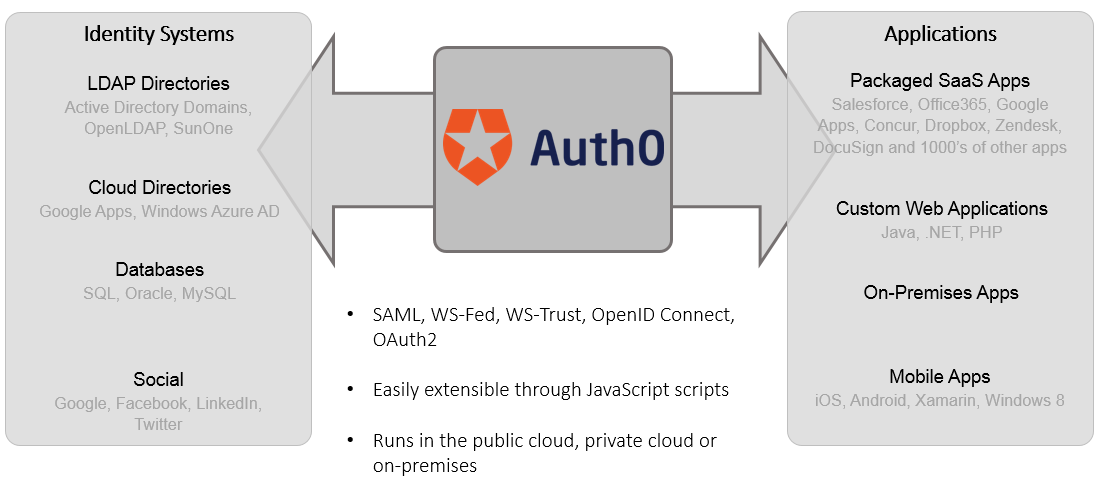
Auth0 is an all-in-one software solution that provides an authentication and authorization management platform that works with almost any digital device on the market. It's also compatible with mobile devices, IoT devices, computers, and applications. It has a lot of cool modules, and it's usually used by companies that support B2B, B2C, and B2E for universal identity. Many fascinating modules make up the platform's primary features. Universal login flow, customer domain, audit logs, universal login, SMS port, white-label manufacturer, brute…
8PingID
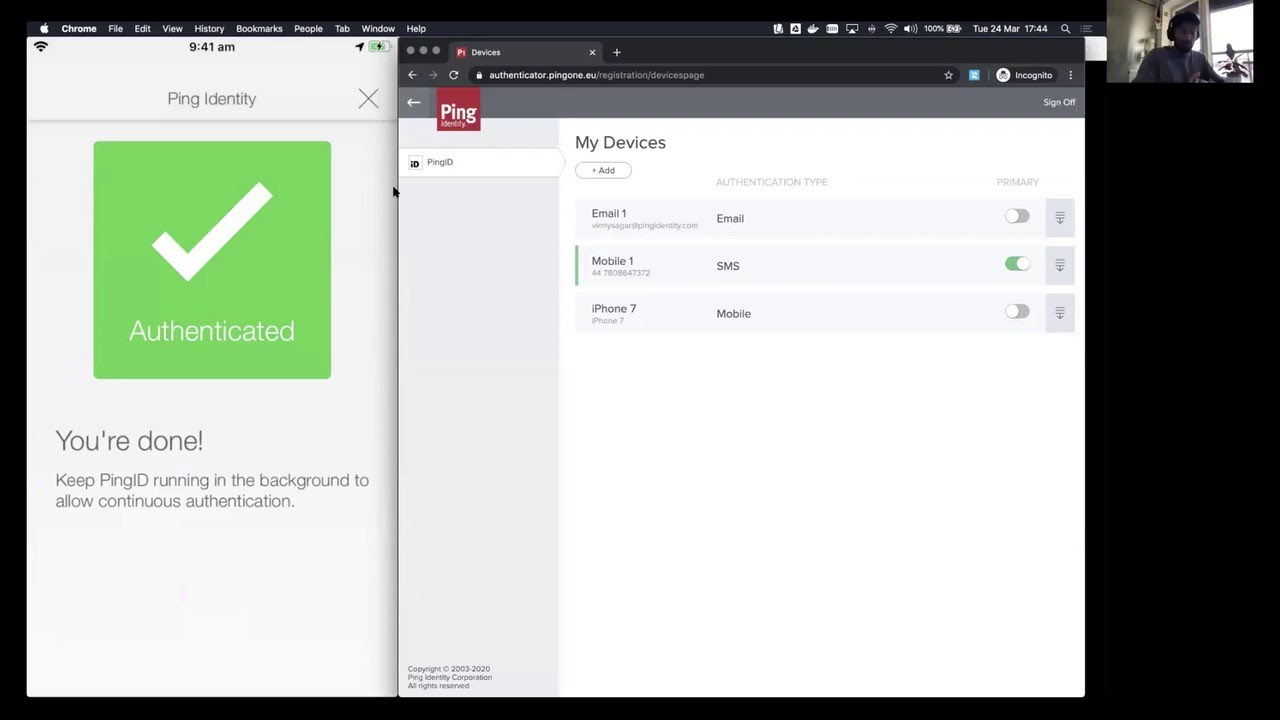
PingID is a cloud-based strong authentication system that lets users log in to apps using their phones. PingID provides an easy-to-use solution for end-users while still providing the protection that administrators want. When strong authentication is required, end-users receive a message on their device, which also includes offline support if the device is not connected to the internet. Its robust network security safeguards networks, individual PCs, services, and businesses. With multi-cloud compatibility, it comes with the necessary digital transformation, allowing…
9Duo
Google Duo is a beautiful, agile, and responsive video calling software with excellent voice quality. People all over the world may use this software to talk and express their emotions with just one click. Google Duo is a simple and dependable application that works on both iOS and Android smartphones, and it's also likely to work on the web. Long-distance communication has never been easier, but Google Duo makes calling and seeing your loved ones a breeze. This lavish program…