AWS Secrets Manager is an Amazon Web series manager that controls the secrets’ life cycle. It allows people to securely encrypt and manage their secrets. People can change database credentials, API keys, and many other secrets by rotating, retrieving, and managing them. People can control all the access to their application services and other resources.
Users can manage multiple security cycles without any upfront investment or ongoing maintenance. It allows various automatic rotation systems, which indirectly increases the security level around sensitive data.
It frequently rotates the security, which reduces the risk of any issue. It also provides an essential Management Service that provides access control through AWS identity and Access management. People can get their 30-day free trial to check their services.
It replicates secrets, which reduces the risk during recovery scenarios. It provides a complete video that gives the details about the working and their security, which is trusted by multiple popular platforms like Autodesk, zoom, and many more.
It is easier to get started with them, or people can contact their experts for any further information or issues. If you are willing to find alternatives, check out our site listing the best alternative to AWS Secrets Manager.
Features
- High-end security.
- Automates multiple tasks.
- Real-time monitoring.
- Provides complete access control.
AWS Secrets Manager Alternatives
1: Devolutions
Devolutions is the service that IT experts and business users use for remote access and corporate password management. Ninety-nine percent of all businesses are small, medium, or micro (SMBs). But most small and medium-sized businesses can't afford or justify the cost or complexity of the best-in-class solutions for privileged access control, password management, and remote connection management (SMBs). It could leave small and medium-sized businesses open to security and compliance breaches, lower their productivity and competitiveness, and even put them…
2: Micro Focus

Micro Focus is a world leader when it comes to business software. It helps thousands of customers in dozens of countries manage the essential IT parts of their businesses so they can keep running even as they change. It does this by giving them mission-critical technology and services to go with it. It helps customers speed up, modernize, simplify, strengthen, and analyze their businesses and operations. It makes it easier for companies to run well and grow. Depending on the…
3: Bravura Security

Bravura Security is the only way to handle Identity Management, Privileged Access Management, and Password Management all at once. Since it offers identity and access management services, it could help protect your organization from threats. At Bravura Security, it provides identification solutions that you can both control and use. It makes your network and internal controls more secure. Doing this gives you the information, tools, and rules you need to improve internal controls and make your management work better as…
4: ARCON

With ARCON's access management services, users can log in with any Identity (interactive, non-interactive, machine, or embedded) and have a smooth experience. ARCON is in charge of putting this whole thing together. These all-encompassing systems cover all software assets, hardware assets, cloud resources, and user identities. ARCON PAM puts a barrier around your most critical digital assets. It can be an operating system, a database, web servers, network gear, telecom devices, Wi-Fi devices, security devices, operational technologies, the Internet of…
5: One Identity

One Identity, a centralized identity and security management platform with an adaptive strategy, is your best defense against cyberattacks. You'll make your organization more resistant to cyberattacks and other risks, making it more likely that sensitive information won't get into the wrong hands. Having only one form of ID is a simple way to keep your safety in check. It might help you standardize how you handle identity management, giving you more control over your organization's most valuable asset: its…
6: Broadcom

Broadcom is the leader in the making, testing, and distributing of software used in hardware and networking infrastructure. It is done by keeping the world's most complicated hybrid environments up-to-date, optimizing them, and ensuring they are safe. It has a complete portfolio of business-critical software at the cutting edge of its industry and offers scalability, agility, and security. The most prominent companies in the world use this software. In addition to the critical data center, networking, software, internet, wireless, storage,…
7: HashiCorp

HashiCorp is a cutting-edge software platform that lets you manage your infrastructure's provisioning, security, connectivity, and operation in the same way, no matter what kind of application you're using. This platform always does a great job of delivering applications on time, and it has set a new standard for self-service automation. You can choose from several options, such as security and infrastructure automation solutions. You have set up robust infrastructure automation to automate provisioning, keep up with compliance requirements, and…
8: Delinea

Delinea is a complete PAM solution for businesses with complex IT systems. It combines the knowledge of two market leaders. Administrators, business users, service accounts, and machine identities have dynamic access restrictions, and all users are treated as privileged users. Based on the ideas of Zero Trust, Delinea only lets people access what they need for a given task and only when they need it. It enables people to freely switch between different settings that are each made for their…
9: BeyondTrust
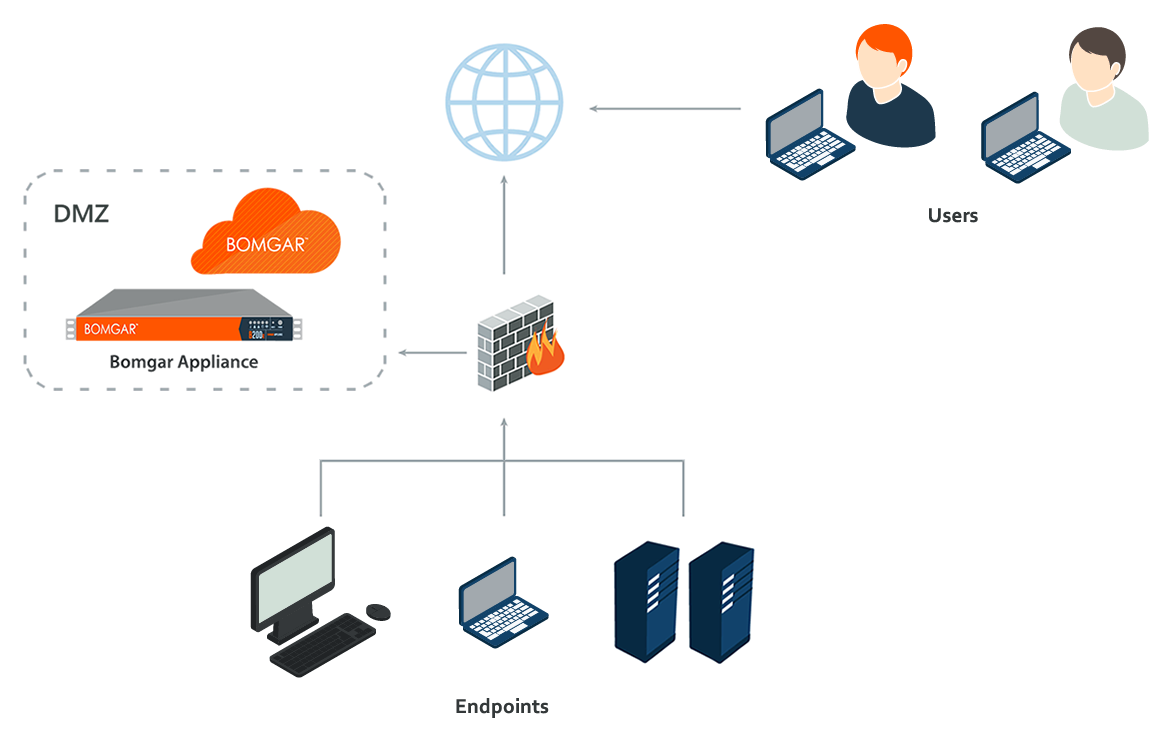
BeyondTrust is the de facto standard for Privileged Access Management. It is the easiest way to stop data breaches caused by lost or stolen credentials, inappropriate use of rights, and unauthorized remote access. If you want the best in this area, you don't have to look further than BeyondTrust. Because the platform is scalable, businesses can quickly add more security to endpoints, servers, the cloud, DevOps, and network devices in response to changing threats. Compliance, risk, and operational performance are…
10: CyberArk

CyberArk is a security system that limits who can get into administrative accounts and makes it less likely that data will be lost. The solution protects the system and its data from threats before they happen. It lets businesses keep track of everything that is going on in privileged sessions. The program protects email attachments and servers from start to finish. It also keeps an eye on servers in real-time and can deal with problems as they come up. The…
