Wifislax is an open-source GNU/Linux Wireless distribution based on Slackware developed by SeguridadWireless.net that is designed for computer security, forensics, and computer system audit. Live Wifislax provides the functionalities of LiveCD and LiveUSB and comes with many security and auditing tools, including port and vulnerability scanners, exploit creation and design tools, forensics analysis tools, auditing tools for wireless, and malware tools, sniffers, and launchers.
Furthermore, it supports a large number of wired and wireless network cards through the integration of various network drivers into the Linux Kernel.
Features
- Wireless Security
- Auditing Tools
- Live CD/USB
- Integrated Network Cards
- Vulnerability Scanners
Similar to Wifislax
There are up to 15 Wifislax Alternatives. It has features like Debian-based OS, Linux Distribution, Penetration Testing, Security Auditing and Ubuntu-based OS. The best alternative to 15-wifislax-alternatives is Kali Linux, which is Free. The other best apps like 15-wifislax-alternatives are Parrot Security OS, Tails and BlackArch.
Pricing
Wifislax Information
15 Best Wifislax Alternatives
Filter Alternatives
1SELKS
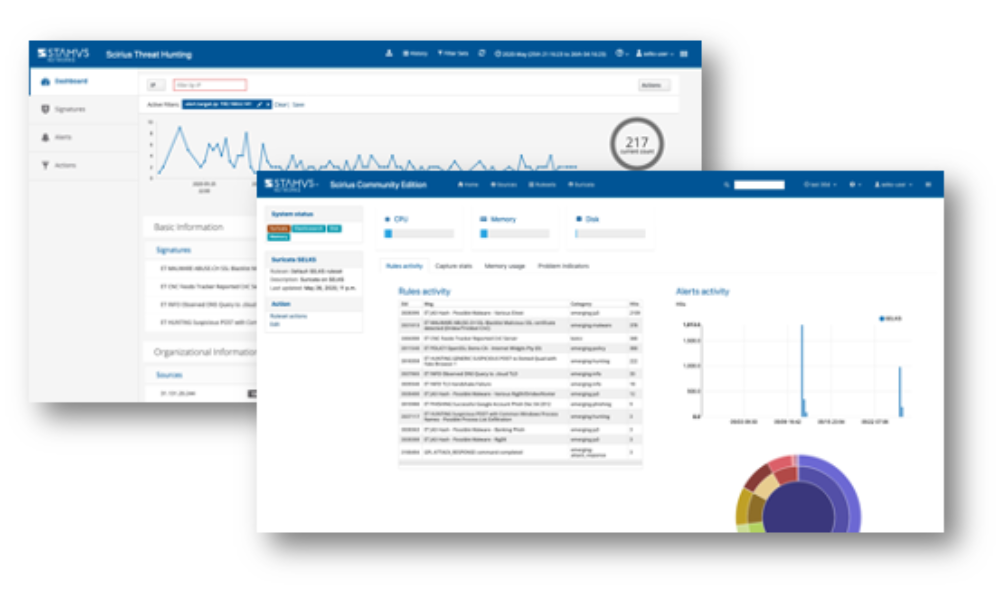
SELKS is an open-source operating system that is a Debian-based live distribution created and maintained by Stamus Network, specially designed for network security management. It's a turn-key Suricata Network Intrusion Detection/Protection System, Network Security Monitoring (NSM), and threat hunting implementation platform. Like other OS platforms, its live distribution is also available as an installable Debian-based ISO or through Docker composed on any Linux OS. Furthermore, SELKS ISOs are available in air-gapped environments, bare metal, and VM installations. This platform is…
2AtlasOS
AtlasOS is an open-source modification of the windows operating system specifically designed to improve performance and latency. AtlasOS – Reforming windows for better fps and lower latency helps to reduce CPU stress by minimizing processing, lowering system latency, improving memory by terminating memory, hogging processes, and increasing storage space. AtlasOS is an operating system with slimmed images of windows with extensive privacy policies to get rid of any spyware or malicious attacks. It removes all kinds of tracking embedded in…
Advertisement
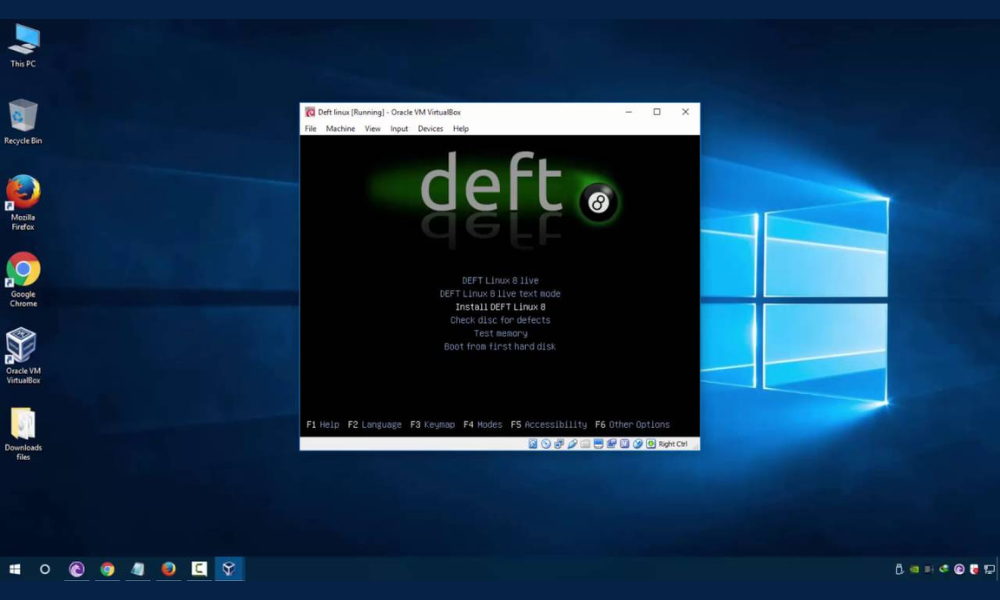
3DEFT Linux
DEFT Linux (Digital Evidence and Forensics Toolkit) is an Ubuntu-based live GNU/Linux distribution mainly used for computer-related forensics as the name describes and Information Technology Security. It's a customized Ubuntu Live Linux CD distribution that contains excellent hardware detection and some open-source applications reserved for computer system forensics, incident response, and security. With this platform, you can open encrypted data and recover lost and deleted data through built-in tools. Furthermore, there is a DART (Digital Advanced Response Toolkit), a graphical…
4Bugtraq
Bugtraq is a type of platform for electronic mailing lists founded by Scott Chasin in 1993 that mainly focuses on the mailing list for the in-depth discussion and announcement of computer security vulnerabilities. Bugtraq is a high-volume mailing list with over 776 posts in a month. The main topics of discussion include vendor security-related announcements, methods of exploitation, and how to solve them. Furthermore, it discloses, discusses, and publishes computer system vulnerabilities regardless of vendor response, including security researchers and…
Advertisement
5CAINE
CAINE, Computer Aided Investigative Environment, is an open-source Ubuntu-based Live Linux distribution managed by Nanni Bassetti, founded in 2008, and used for Digital Forensics and Incidence Response (DFIR). And CAINE Linux offers a forensic environment that integrates software tools as modules with powerful scripts to give users a friendly Graphical User Interface (GUI). CAINE Live USB/DVD – computer forensics digital forensics comes with an interoperable environment that supports the investigator during the four phases of the procedure of digital investigation.…
Network Security Toolkit is an open-source Linux distribution Live DVD/USB Flash Drive founded by Ronald W. Henderson and Paul Blankenbaker. NST offers free computer security and networking tools to perform or improve routine security, network diagnostic, management, and monitoring. This toolkit can also be used as a server's network security analysis, validation, and monitoring tool. Network Security Toolkit (NST 34) provides network traffic analysis, intrusion detection, monitor bandwidth, serial port monitoring, wireless network monitoring, network packet generation, virtual system service…
Advertisement
Like Network Security Toolkit, Fedora Security Spin, now known as Fedora Security Lab, is an open-source Ubuntu-based platform that provides security auditing, computer forensics, system rescue, and teaching security methodologies in organizations. The platform has an Xfce desktop environment and menu that provides all the tools and instruments needed to check security or recover the system. Furthermore, you can run the system from a USB stick, install and update software, and permanently save your test outcomes. Security Lab – Fedora…
8Dracos Linux
Dracos Linux is an open-source Linux-based operating system that comes with a pack of pentest tools, including information gathering, forensics, malware analysis, access persistence, reverse engineering, privilege escalation, and more. Dracos Linux is based on Linux from scratch and in the protection of GNU General Public License, and it's a variant of Linux Distributions. Furthermore, you can use it to perform penetration testing, ethical hacking, and cybersecurity tools. It's a Pentesting distribution suite that comes with packages like gobject-introspection, ISC…
9Cyborg Linux
Cyborg Linux is a most advanced & powerful Linux distribution based on the Ubuntu Platform that provides you a wide variety of penetration testing and cybersecurity tools for Ethical Hackers, IT professionals, and Cyber Security Experts. Cyborg Linux is integrated with a stable Linux environment and 700+ tools and dedicated tools for mobile security and malware analysis. Cyborg Hawk Linux can be used as a live operating system and also comes with an exploitation toolkit, stress testing, reverse engineering, forensics,…
10Matriux
Another open-source Linux-based Operating System, Matriux, can be used for penetration testing, forensics, and ethical hacking. Furthermore, it can be used for system and network administration, cyber forensics investigations, security investigation, vulnerability analysis reverse engineering, and more. Mainly it is used by security enthusiasts and IT professionals; you can also use it as a default desktop system. With this OS, you can convert your system into a penetration testing and hacking toolkit without installing any kind of software. You can…
11BackBox Linux
BackBox Linux is an open-source Ubuntu-based Linux distribution that comes with a network & informatic system analysis toolkit that can be used for security assessment, ethical hacking, security testing, and penetration testing. The main focus of BackBox Linux is to promote the culture of security in the IT environment to make a better and safer experience for penetration testers and hackers. BackBox is a non-profit organization that offers a range of penetration testing services to simulate an attack on your…
12BlackArch
BlackArch is a Linux-based platform for penetration testers and security researchers that comes with a repository of almost 2800+ tools to ensure cybersecurity in all your developments and can be installed individually or in groups. BlackArch Linux – Penetration Testing Distribution is a similar platform working to Parrot OS and Kali Linux, but it is based on Arch Linux instead of Debian. BlackArch comes with packages & tools along with their dependencies, and you can run it as a live…
13Tails
Tails, The Amnesic Incognito Live System is a portable & Debian-based Linux Distribution operating system that ensures security, privacy, and anonymity. Tails provide an amazingly unique environment where you shut down your computer, start your Tails USB stick, and turn your computer into a secure machine. And it leaves no digital footprints, and everything you do disappears automatically when you shut down Tails. It also has storage, and you can save your documents, files, browser bookmarks, emails, and additional software…
14Parrot Security OS
Parrot Security OS is a Linux Distribution Operating System with 600+ tools that developers can use for attack mitigation, security research, forensics, and vulnerability assessment. Parrot Security consists of tools, utilities, and libraries that can be used for penetration testing, security assessment, and security of assets in a reliable, flexible, and reproducible manner. Parrot Security OS provides you with a convenient Debian environment with all the tools you ever need without any errors. This platform has many editions, including Home…
15Kali Linux
Kali Linux is a Debian-based open-source Operating System and a Linux distribution developed by Mati Aharoni and Devon Kearns, maintained by offensive security that helps developers & hackers to do penetration testing. The main focus of the founders is to enable kernel auditing; formerly, it is named Kernel Auditing Linux. And it has around 600 penetration testing tools, most famous of which are Armitage, Nmap, Wireshark, John the Ripper, Metasploit, Aircrack-ng for cyber-attacks, penetration testing, SQL injection, wireless LANs, and…